Fraud theft has many faces – none of which are pretty – but perhaps the most insidious is that of Rouge Anti-Virus Software scams.
One of the newest virus threats online comes to your computer as a true “wolf wrapped in sheep’s clothing.” System Tool 2011, and other such malware, is being e-mailed to computers all over the world, causing damage and bilking its victims out of hundreds of dollars.
The Scam
Unless you work, live, and breathe for computers, you probably aren’t familiar with online theft information regarding the term “rogue” anti-virus software until you become a victim. This is not optimal way to learn about the deleterious effects it can have on your computer and bank accounts.
Rogue anti-virus software is spread over the Internet the same way other viruses are: in e-mail attachments, as a part of a shareware software bundle all with the help of a Trojan. (Trojans are software packets that sneak inside your hard drive hiding within another download, much the same way the actual warriors hid inside the horse.) One of the most successful, and most damaging, of these rogue anit-virus programs is System Tool (also known as systemtool and System Tool 2011).
Rogue anti-viruses have no affinity for malware, Trojan, or other harmful programs’ removal because they are in and of themselves malware. Their real and only purpose is theft fraud by capturing your credit card information under false pretenses. This qualifies rogue virus software as identity fraud theft scams at their finest.
How it Works
Once inside your computer, System Tool, or any other rouge anti-virus program, springs into action without your knowledge or consent. It self-installs and plants its malignant files deep within your registry. It sets itself to begin on your computer’s start up.
The next time you turn on your computer you will be greeted with a legitimate-looking scan results screen listing the many programs System Tool has detected within your computer. The list is fake – a scare tactic to motivate you to click the removal button option.
Once you click the remove button, a message will prompt to you to activate your account or subscription. To do this you need to pay for a one, two, or lifetime subscription option. To keep you motivated, new messages are popping up all the while proclaiming new infestations, infected files, and other damages needing repair.
Don’t fall for it. The messages are fake. The infections are fake. The computer scan results are also fake. They are all part of System Tool’s design to entice you to impart of your credit card information willingly. This program is a virus itself, so it will not do anything but mess up your computer and then take your money and run.
Recovery
First off, if you have paid for System Tool (now that you are wiser), call your credit card company and dispute the charges.
The next step is getting it off of your computer. This can be tricky because part of the programming is aimed at keeping itself alive inside your hard drive by blocking attempts to remove it. Legitimate virus removal software does not always recognize and remove it because the malware looks like real anti-virus software.
To be certain you are rid of System Tool, you will most likely need the help of an experienced computer wiz, a visit from the Geek Squad, or someone similarly qualified.
The process of starting the computer in safe mode and sifting through real system files from fake ones will be simple for them but difficult and dangerous for a novice.
Thursday, December 30, 2010
Fraud Theft by Rouge Anti-Virus Software
Posted by
SofiaBrown185
5:05 AM
Tuesday, December 28, 2010
How to Remove Disk Doctor (Virus Removal Guide)?
Posted by
SofiaBrown185
4:56 AM
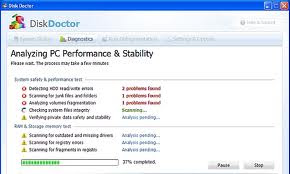 In order to uninstall Disk Doctor you’ll need Malwarebytes’ Anti-Malware tool
In order to uninstall Disk Doctor you’ll need Malwarebytes’ Anti-Malware tool
1. First and foremost you should print out the following instructions as you may be asked to close all open windows later on in the cleaning process.
2. You might encounter downloading issues if your computer is infected with Disk Doctor, so it’s possible you won’t be able to download anything on your own computer. If this is the case, you’ll need to download the specific files for the removal procedure on another computer and then transfer them using a CD/DVD, a flash drive or an external drive.
3. In order to proceed with the cleaning, you must first close any active processes that belong to Disk Doctor so they won’t interfere. You can do that by downloading RKill from this link. Remember to use the iExplore.exe download link, and save the program on your desktop.
4. Next, open the iExplore.exe file, and the program will begin to automatically close all processes associated with Disk Doctor and other Rogue programs as well. It’s important that you let RKill finish running, even if at some point it will display a message that RKill itself is an infection. Again, this is another fake message from Disk Doctor that might even stop the process and close RKill. In case this happens, the first method of tricking Disk Doctor is by not closing the warning window, instead leaving it on the screen and running RKill once more. If RKill still hasn’t managed to run all the way to the finish point, try running it a couple more times, until the malware is no longer running on your computer. If after all this, you still encounter problems in running RKill all the way, try downloading a renamed version of RKill here, which is in fact simply a renamed copy of RKill. After RKill will eventually finish its job, do not reboot you computer as the malware programs will pop out again.
5. After you get rid of all Disk Doctor associated processes, download Malwarebytes’ Anti-Malware (MBAM) from the link provided above and, once again, save it on your Desktop.
6. After the download has finished, close all programs and windows on your computer (including this one).
7. Open the file mbam-setup.exe from your desktop to start installing MBAM on your computer.
8. In order to complete the installations you just need to follow the prompts and you must remember not to make any settings changes along the way. When the installation process finishes, keep in mind to leave both the Update Malwarebytes’ Anti-Malware and Launch Malwarebytes’ Anti-Malware checked. After you hit the Finish button be very careful not to reboot your computer even if Malwarebytes’ asks you to.
9. After you finish the installation, MBAM will automatically start with a message that advises you to update the program before performing any scan. Once you hit the OK button a new window with the main program will appear as shown below:
10. On the Scanner tab choose Perform full scan and click the Scan button.
11. The scanning process can take quite a while, so be patient while you’re staring at a window like the one below:
12. When MBAM has finished scanning your computer, hit the OK button from the message window that will appear.
13. You’ll now be sent back to the main Scanner screen where you should select Show Results.
14. A window with all the malware that MBAM discovered will be seen, like the one provided below. You must now press the Remove Selected button and MBAM will start deleting all files and registry keys and will add them to the programs quarantine. MBAM might require you to reboot the computer at some point in order to remove some files and you must allow the program to do that.
15. When MBAM has finished removing the malware, a Notepad scan log will be displayed. After you close the Notepad Window, you can exit the MBAM program.
16. Disk Doctor should now be completely removed from your computer, but we strongly recommend that you also scan the computer for vulnerable programs (you can use Secunia PSI to that end), as many rogues and malware are installed through out-dated and vulnerable programs. Hope this guide turns out helpful. Please let us know if you successfully removed Disk Doctor.
Friday, December 10, 2010
How to remove HDD Diagnostic Malware/Virus?
Posted by
SofiaBrown185
4:26 AM
 HDD Diagnostic is a rogue (malware, virus) parading as a system optimizer software that, once installed, tries to convince users there is something wrong with their system by displaying various fake error messages.
HDD Diagnostic is a rogue (malware, virus) parading as a system optimizer software that, once installed, tries to convince users there is something wrong with their system by displaying various fake error messages.
HDD Diagnostic is installed via Trojans or the TDSS Rootkit. Don’t worry, this removal guide will also show you how to get rid of the TDSS Rootkit.
Once installed, HDD Diagnostic will start every time you log into Windows and it will display error messages when the user tries to launch any program or delete files. It will then ask you to analyze your system with the program and, if you do that, it will display numerous warnings and errors that can only be fixed if…surprise, surprise…you buy the full version of HDD Diagnostic. Of course this is a scam so don’t be tricked into giving your credit card info.
HDD Diagnostic Removal Guide
If HDD Diagnostic prevents you from downloading files, you need to get them on an uninfected system and transfer them via USB, CD/DVD etc.
1. Launch iExplore.exe in order to stop all the processes associated with HDD Diagnostic. It might take a while but you’ll know that iExplore has finished when the black window disappears.
Note: You might receive some messages saying that iExplore.exe is a virus. Don’t worry, this is just HDD Diagnostic’s way of defending itself. If such a message appears leave it on the screen and run iExplore.exe again. If you’re still having problems download RKill.com and/or eXplorer.exe from the provided link and try again ( they are just renamed copies of iExplore.exe )
2. Execute the downloaded MBAM ( Malwarebytes’ Anti-Malware ) setup file and complete the installation following the on-screen instructions ( just make sure that both “Update Malwarebytes’ Anti-Malware” and “Launch Malwarebytes’ Anti-Malware” boxes are checked ).
Attention ! Don’t reboot your system even if MBAM prompts you to as you’ll have to start over.
3. Once the installation finishes MBAM will automatically start. Select Scanner, then Perform full scan and click Scan. The scanning process might take a while.
4. When the scan finishes click on Show Results, make sure every box is selected and then hit the Remove Selected button. Good Job!
You can now restart your system as HDD Diagnostic should be removed by now.
Monday, November 15, 2010
Microsoft vs. McAfee: How free antivirus outperformed paid
Posted by
SofiaBrown185
2:47 AM
Ed Bott has experiment. He come to know how effective is free antivirus software? Ed Bott had a chance to see a real, in-the-wild example just this month, and the results were, to put it mildly, unexpected. The bottom line? Microsoft’s free antivirus solution found and removed a threat that two well-known paid products missed. Here are the details.
Ed Bott’ve had Microsoft Security Essentials (MSE) installed on my main working PC for most of the past year. Mostly, he use it for real-time protection. He typically disable the scheduled virus scans on PCs and instead occasionally do a manual scan just to confirm that nothing out of the ordinary has snuck through. Last month he decided to perform a scan using the Full option.
MSE had detected several files that it considered malicious. One was a rigged PDF file. The other was a single file in the Java cache folder on this system that contained three separate exploits. Using the information in the MSE history pane, he found the file and uploaded it to Virustotal.com, which is a free service that allows you to scan a suspicious file using 43 separate antivirus engines. The file, identified by a unique hash, had already been analyzed:
Only 17 of 43 antivirus products detected this as a threat. The full results page showed the identification, if any, for each product on the list. Microsoft, Symantec, Avast, and F-Secure were among the engines that flagged the file. But the majority didn’t. That means one of two things. Either the file was a false positive, or he was about to delete something harmless and perhaps even necessary. Or it was real, and most AV programs were missing it.
To get to the bottom of the issue, he sent e-mail messages to contacts at three companies. He asked Microsoft to reanalyze the file and confirm that it was indeed malicious. He also asked McAfee and Sunbelt to look at the file; both of them had reported the file as clean, according to VirusTotal.
Microsoft had two analysts review the file. Here’s a portion of their response:
We have confirmed that the threat detection you received from Microsoft Security Essentials is indeed valid. There were more than 3.5 million reported CVE-2008-5353 attacks in Q3 2010, and Java vulnerability exploitations like these, while once a rare occurrence, have spiked this year. … [T]his exact file is something we have seen in the wild more than 40,000 times in the past six months.
This October 18 post by Holly Stewart on the Microsoft Malware Protection Center blog provides useful additional detail on why these types of attacks can be challenging for IDS/IPS vendors, as well as the steps customers should take to ensure that they are protected.
According to the scan results, this threat was first identified in definition 1.85.1774.0, which was released by Microsoft on July 9, 2010.
McAfee responded quickly to my e-mail as well. A spokesperson sent this reply:
Our Labs team took a look at the file you referenced and it is malicious. We are in the process of developing new heuristics to combat the effects from a stream of recent malicious JAR files more proactively, the file corresponding with the hash you mentioned is in the queue.
Sunbelt’s Malware Response Manager, Dodi Glenn, reported that this file was in the company’s repository and submitted it for detailed analysis. Here are the results:
This file contains a malicious java.class … that exploits the CVE-2008-5353 vulnerability. … We are currently testing our updated detection for this exploit and expect to release it shortly.
The good news is that my system wasn’t compromised in any way. The exploit in question was blocked by a Java update that I had installed last year. Likewise, the booby-trapped PDF file (which all of the antivirus programs detected) relied on the user having a very outdated version of Adobe Reader installed, and mine was fully up-to-date.
Last week, when I wrote about Microsoft’s decision to expand its distribution of Microsoft Security Essentials via Microsoft Update, McAfee complained that free software simply isn’t as good as its paid protection. Here’s what a spokesperson told me:
McAfee wants consumers to be safe online. Options that provide an elementary level of security are free products including Microsoft Security Essentials, however these mostly rely on traditional protection mechanisms. McAfee products offer not only more features but most importantly, McAfee products offer real-time protection using cloud-based Global Threat Intelligence to combat even the most sophisticated threats thus ensuring complete protection and peace of mind.
In this case, at least, that protection wasn’t as complete as the free Microsoft product it was comparing itself to.
As an aside, it’s worth noting that criticizing Microsoft Security Essentials because it’s free misses an important point. MSE uses the same scanning engine and definitions as its enterprise-grade Forefront product, which is most assuredly not free.
One certainly shouldn’t draw definitive conclusions from a single anecdotal example, but as this case shows, the gap between antivirus products isn’t as simple as free versus paid, and even the best and brightest researchers can miss a threat.
Resource:http://www.zdnet.com/blog/bott/microsoft-vs-mcafee-how-free-antivirus-outperformed-paid/2614
Friday, October 22, 2010
McAfee 2011 Releases Total Protection with $20 Discount
Posted by
SofiaBrown185
12:15 AM

McAfee, Inc. announces the new McAfee® Total Protection 2011 at a discount of $20.
With thousands of new virus threats created every day, depends on traditional security updates isn't good anymore. McAfee Active Protection™ technology instantly analyzes and blocks new virus threats in no time so there's virtually no gap in your protection.
McAfee® Total Protection 2011work with minimal interruptions with fast and effective virus, malware, and spyware scanning. Provides schedule security scans when you're not using your PC, automatic scans and updates occur when your system is idle. McAfee® Total Protection won't slow you system performance.
The Home Screen gives you all the information you need at a instant. And you're never more than one click away from it, which removes popup windows and makes for easy navigation. Simplified alerts and scan results make it easier than ever to protect your PC.
Thursday, October 14, 2010
Symantec launches beta of Norton 360 5.0
Posted by
SofiaBrown185
8:41 PM
 Symantec opened the public beta of Norton 360 5.0, the latest version of the company's end-to-end security suite. This beta builds upon the updated versions of Norton Antivirus and Norton Internet Security, and improves the usability and performance in the backup and tune-up features exclusive to Norton 360, revamps the online backup user experience, and integrates with Norton's free online tools.
Symantec opened the public beta of Norton 360 5.0, the latest version of the company's end-to-end security suite. This beta builds upon the updated versions of Norton Antivirus and Norton Internet Security, and improves the usability and performance in the backup and tune-up features exclusive to Norton 360, revamps the online backup user experience, and integrates with Norton's free online tools.
New Features
The revamped UI in Norton 360 puts all of the different tools: Antivirus protection, online backup, Identity protection, Norton Safe Web, Norton Online Family, automatic PC tune-up and the global threat protection map are all displayed on the main screen, and settings/security controls for each are organized underneath.
Norton 360 5.0 now includes resource management for third-party apps on your PC. Norton 360 can immediately alert you, if a particular piece of software you have installed is using a lot of system resources. If alerts aren't your thing, you can check out resource logs to compare third party app behavior.
As with any security package, performance remains a paramount issue. Symantec says it is working to improve backup and restore performance, reduce system impact, and increase valuable communication with users in Norton 360. PC Tuneups, one of the most popular features of 360 are also faster, the company told us.
Additionally, the Bootable Recovery Tool Wizard, Norton's malware removal tool to get inoperable systems up and running again, can now be booted from USB or CD/DVD.
Friday, October 8, 2010
How To Remove The Conficker Virus Removal Guide
Posted by
SofiaBrown185
12:14 AM

UK’s daily The Register has been reporting (here) that 3 out of 10 computers running Windows are facing ConfickerWorm attacks. According to Wikipedia, it uses flaws in Windows software and Dictionary attacks on administrator passwords to co-opt machines and link them into a virtual computer that can be commanded remotely by its authors.
Conficker vhas since spread rapidly into what is now believed to be the largest computer worm infection since the 2003 SQL Slammer, with more than seven million government, business and home computers in over 200 countries now under its control.
The worm has been unusually difficult to counter because of its combined use of many advanced malware techniques.
Two variants of Conficker affected computers connected to the global networks. During early November 2008, Conficker was launched and propagated via Internet exploiting a vulnerability in a network service (MS08-067) on various Windows versions: Windows 2000, Windows XP, Windows Vista, Windows Server 2003, Windows Server 2008 including Windows Server 2008 R2 Beta.
In response to this, Microsoft released an emergency out-of-band patch on October 23, 2008 to close this vulnerability in Windows 7 (public beta). Despite all these, a large number of Windows PCs estimated to be around at 30% continued to remain unpatched as late as January 2009.
The second variant of the Confiker worm was discovered on December 2008. It added the ability to propagate over LANs through removable media and network shares allowing the worm to propagate quickly and by January 2009, the estimated number of infected computers ranged from almost 9 million to 15 million.
According to Antivirus software vendor Panda Security, 2 million computers analyzed through ActiveScan reports around 115,000 (6%) were infected with Conficker .The worm continues to change in its propagation activity and update strategy of recent variants. This how-to focuses on removing the Conficker Worm as well as the relation between Conflicker and fake Antivirus protection software.
Source:- techmagnews.com
Partners Links
Labels
- About MSN Virus Removal (1)
- antimalware (1)
- antivirus (2)
- antivirus protection (1)
- antivirus security (1)
- best antivirus (1)
- Computer Virus Removal (2)
- Computer Virus Removal Guide (1)
- computer vurus check guide (1)
- Conficker virus removal (1)
- ConfickerWorm attacks (1)
- download antivirus (1)
- firewall (1)
- Folder Exe Virus Removal Advices (2)
- install antivirus (1)
- Internet Explorer (1)
- Internet Security Software (1)
- legitimate anti-spyware (1)
- McAfee (1)
- McAfee Antivirus (1)
- McAfee Support (2)
- MSN Virus Removal (1)
- Panda Global Protection 2011 (1)
- PC software (1)
- pc Virus Removal (1)
- Professional Computer Virus Removal Program Review (1)
- Remove a Worm Virus (1)
- Remove Antimalware Doctor Virus (1)
- remove malware (1)
- remove spyware (1)
- Remove the Pendrive Virus (1)
- rogue anti-spyware (1)
- Spyware protection (1)
- virus and worms (1)
- virus protection (1)
- virus removal (1)
- Virus Removal - Why and How (1)
- Virus Removal Advices (1)
- Virus Removal help (3)
- virus removal support (1)
- Virus Removal tech support (1)
- Virus Removal Tips (1)
- virus security (1)
- virus threat (2)
- worms (1)